DST Root CA X3 Expired: As a reminder, the current root certificate used by "Let's Encrypt", the IdentTrust DST Root CA X3 certificate, expired on September 30, 2021. You may not need to do anything about Root CA expiring, but I'm guessing something would have broken down that day, so here I am in this article for DST Root CA X3 Expiration I am going to give complete information about For this you will be with us till the end.
DST Root CA X3 Expired
For information, let's tell you that on Thursday, 30 September 2021, several websites and services faced problems due to the expiration of the root certificate provided by Let's Encrypt, one of the leading suppliers of HTTPS certificates. According to Scott Helme, founder of Security Headers, the IdentTrust DST Root CA X3 expires at around 10 p.m. ET. He is following the situation and noted that Let's Encrypt is used by millions of websites. Some older devices will be unable to check certain certificates without them.
If you do not know about Let's Encrypt, then let us tell you, "Let's Encrypt" is a free non-profit organization that ensures secure and encrypted communication between your device and the Internet. Despite advance notice that the deadline would be September 30, dozens of users experienced problems with several services and websites when the deadline approached.
DST Root CA X3 Expiration
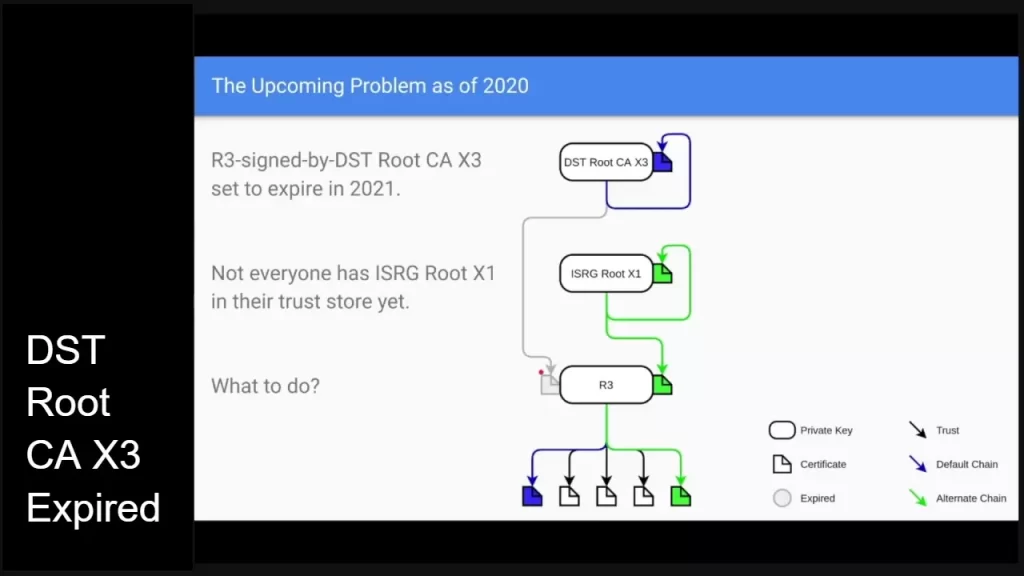
For information, let us tell you that the certificate trust trusts the certificate (and intermediate certificate) that issued the "root" on your computer. Root Certificate generates an intermediate certificate, which is then used to generate a generic certificate for your website. This is called a "trust chain". This chain will validate your certificate (also known as a leaf or end-entity certificate). Let's Encrypt's previous root certificate DST Root CA X3 (and its R3 Intermediate) expired on September 30, 2021. Their ISRG Root X1 certificate has replaced it (and has been replaced by R3 Intermediate).
Possible DST Root CA X3 Expired Issues
As you know, the certificate may be considered untrusted or invalid in some cases due to the expiration of the original certificate (and its link to the expired R3 Intermediate certificate). To remedy this, instruct your server to use (service) the appropriate chain. In some circumstances, the problem is caused by the client computer. The R3 Intermediate Signing Certificate, which is linked to the DST route CA X3, expired on September 29 at 19:21:40 2021 GMT. The DST Root CA X3 Root Certificate expired on September 30, 2021 at 14:01:15 GMT.
Also note that Windows may initially serve a legacy chain designed for Android compatibility when DST Root CA X3 expires, we have confirmed that if ISRG Root CA X1 (self-signed ) is also available in the Trust Store, will return to the Contemporary chain immediately upon detection. DST Root CA X3 has expired. There is a solution available. This means that earlier operating systems that did not rely on ISRG Route X1 would not be served content by Windows services such as IIS. If you need legacy support without a solution, change the certificate authority.
Workaround For DST Root CA X3 Expired
#1 Fixes for servers and how to change chains before (or after) expiration
To begin, we recommend taking the following actions to repair your server's certificate chain:
- Use the in-app update process or download the current version of Certify The Web from https://certifytheweb.com. Even if you are not currently using this app, the upgrade will automatically resolve frequent trust store concerns (and it can then be uninstalled if not being used).
- Restart the server (this forces windows to re-evaluate the served certificate chains). You might be able to prevent the reboot by simply restarting IIS using iisreset /restart.
- Using a chain checker, verify your certificate chain.
- In some circumstances, you may need to renew your IIS bindings; the simplest option is to alter the certificate and update the bindings by clicking 'Request Certificate.'
Depending on the condition of your server's trust store, Windows will serve one of two chains:
- Chain 1 (modern) : (your cert) > R3 > ISRG Root X1
Current operating systems support this chain.
- Chain 2 (legacy) : (your cert) > R3 > ISRG Root X1 > DST Root CA X3
If you need to work with earlier operating systems, such as Android 7.1 and lower, this chain is ideal. On Windows, this chain is tough to support.
For IIS and other web servers, you can only serve one of these chains per Windows server (computer), not a mix. The modern chain will be provided through Certify The Web's default trust store maintenance. Unless it was already installed, you may need to import the cross signed ISRG Root X1 if you need the legacy chain (see Switching to Chain 2, below).
Note: If you're still seeing this old chain after the DST Root CA X3 expires (after you've updated Certify The Web and rebooted), you need to fix it right away. At the very least, use certlm.msc to make sure ISRG Root X1 (Self signed) is installed under your machine's Trusted Certification Authorities and remove the R3 given by DST Root CA X3 from Intermediate Certification Authorities.
#2 Servers that aren't IIS (Apache, nginx etc on Windows or Linux)
Check that your service is set up to use your certificate, including the private key and chain. These services will work without pointing to a chain file, but in the case of an expired R3 (because you haven't given it to them), your customers may attempt to resolve the R3 themselves (since you haven't given it to them), and they may resolve it to the old (expired) one.
#3 Users (browsers etc)
If your site works on most devices but not on others, the issue is most likely with their trust store (their list of trusted root certificates).
#4 PCs that run on Windows
Simply visiting a website with Chrome, Edge, or another browser on a Windows PC updated the client trust store with the appropriate certificates. When you visit https://valid-isrgrootx1.letsencrypt.org/, Windows will immediately add ISRG Root X1 to its trust store.
#5 macOS, iOS, and so on
Even if your server is no longer using the expired R3 > DST Root CA X3 chain, some operating systems keep it. Restart the client device that is impacted.
#6 Java-based systems, for example
Some programmes keep their own trust database. You may need to update your system's trust store to include the latest ISRG Root X1 certificate. Any system that cannot be updated must view the legacy chain, or the CA must be switched.
Related searches
- dst root ca x3 expired
- dst root ca x3 expiration
